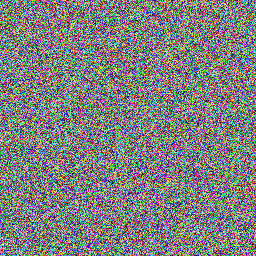(Quick reminder, before it becomes obvious from the text — I have more interest in hardware random number generation than I have understanding …)
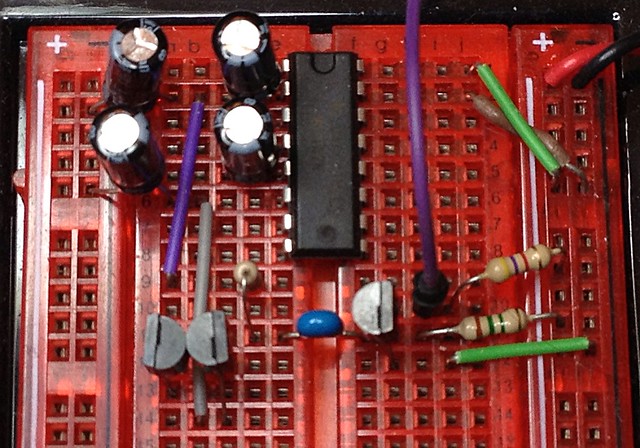
Just got Bill “WaywardGeek†Cox’s Infinite Noise USB Random Number Generator. It uses very few components, and doesn’t even have a microcontroller on board. It relies on the controlled amplification of thermal noise as its entropy source.
As it’s so very simple, it uses a driver to read from the device, and then hashes the data to reduce the data stream to very close to pure noise. Building the driver is easy, once you work it that the code lives in the infnoise/software folder on the author’s github repo.
Normal operation would look like this:
sudo ./infnoise | entropy_consuming_program …
as in
sudo ./infnoise | rngtest -t 10
which I left running for a work day to get
… rngtest: bits received from input: 10327720032 rngtest: FIPS 140-2 successes: 515955 rngtest: FIPS 140-2 failures: 431 rngtest: FIPS 140-2(2001-10-10) Monobit: 63 rngtest: FIPS 140-2(2001-10-10) Poker: 61 rngtest: FIPS 140-2(2001-10-10) Runs: 162 rngtest: FIPS 140-2(2001-10-10) Long run: 151 rngtest: FIPS 140-2(2001-10-10) Continuous run: 0 rngtest: input channel speed: (min=29.022; avg=178.828; max=19531250.000)Kibits/s rngtest: FIPS tests speed: (min=17.403; avg=30.153; max=85.917)Mibits/s rngtest: Program run time: 56727702860 microseconds
So from its success to failure rate, it produces pretty decent (for my casual use) results. These bytes chug out at around 22¾ Kbytes/second; not screamingly fast, but decent, considering the very simple hardware.
You can run the hardware without hashing/whitening, and the results (from a much shorter run) are less solid:
sudo ./infnoise --raw | rngtest -t 10 … rngtest: bits received from input: 15499264 rngtest: FIPS 140-2 successes: 0 rngtest: FIPS 140-2 failures: 774 rngtest: FIPS 140-2(2001-10-10) Monobit: 0 rngtest: FIPS 140-2(2001-10-10) Poker: 774 rngtest: FIPS 140-2(2001-10-10) Runs: 774 rngtest: FIPS 140-2(2001-10-10) Long run: 0 rngtest: FIPS 140-2(2001-10-10) Continuous run: 0 rngtest: input channel speed: (min=27.201; avg=355.760; max=9765625.000)Kibits/s rngtest: FIPS tests speed: (min=24.868; avg=30.488; max=41.554)Mibits/s rngtest: Program run time: 49831593 microseconds
Another naïve test is seeing how images made from the data stream look:


Each of these 128 pixel squares should be no less than 49152 (= 128 × 128 × 3) bytes — plus the size of any PNG header/metadata — in size. The fact that the raw output is smaller shows that PNG’s compressor found some patterns it could work with.
It’s a fun little device, and Bill is adding new code and features to the driver at waywardgeek/infnoise regularly.